Table of contents
- 1. What is an API ?🙄🙄
- 2. What is API Testing?⚗🧪🔬
- 3. Why an API security important?💁♂️💁♀️
- 4. Why should we do API Testing?🎯🎯
- 5. How to Perform API Testing?🛠
- 6. Types of API Testing📊
- 7. API Testing Tools🔧
- 8. What is WAF(Web Application Firewall) & Why WAF is important👨💻🔥
- 9. Limitation of WAF(Web Application Firewall)?🚧🔥
- 10. What is CherryBomb ?💣
- 11. What is BLST (Business Logic Security Testing) ?👨🔬👩🔬
- 12. Practical Demo👨🏫👩🏫
1. What is an API ?🙄🙄
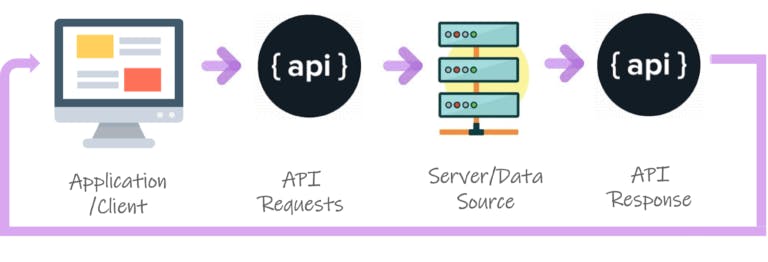
API is the acronym for Application Programming Interface, which is a software intermediary that allows two applications to talk to each other. Suppose you are searching for a flight booking through an online travel booking site. Using the site’s online form, you will fill the necessary information like the flight agency you want to select in, check-in and check-out dates, destination, flight class and number of passengers. Then you click “search.”. But what’s going on between entering your information to receiving your flight choices? APIs, that’s what! The site aggregates information from many different flight agency. When you click “search,” the site then interacts with each agency’s API, which delivers results for available flights that meet your criteria. And all this happens in seconds because of an API, which acts like a messenger that runs back and forth between applications, databases, and devices.
2. What is API Testing?⚗🧪🔬
API testing is a type of software testing where application programming interfaces (APIs) are tested to determine if they meet expectations for functionality, reliability, performance, and security. In simple terms, API testing is intended to reveal bugs, inconsistencies or deviations from the expected behavior of an API. Commonly, applications have three separate layers:
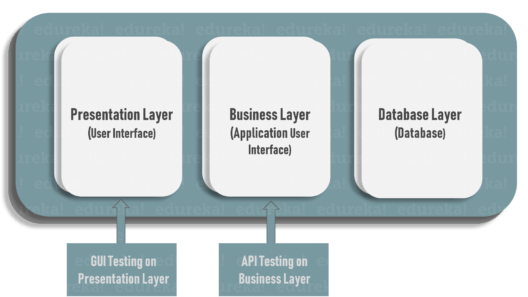
- Presentation Layer or user interface
- Business Layer or application user interface for business logic processing
- Database Layer for modeling and manipulating data
3. Why an API security important?💁♂️💁♀️
API security is important because businesses use APIs to connect services and to transfer data, and so a hacked API can lead to a data breach. API abuse issues have roughly doubled over the past 4 years, according to the 2019 Application Security Risk Report by Micro Focus Fortify. The 2018 data show 35% of the analyzed Web applications had API abuse problems, and the incidence increased to 52% for mobile applications.
4. Why should we do API Testing?🎯🎯
API testing is an important activity that testing teams should focus on. It offers a number of advantages over other kinds of testing
Language Independent: Data is exchanged via XML and JSON, so any language can be used for automation, independent from the languages used to develop the application.
GUI Independent: API testing can be done to check the core functionality of the application to expose small errors and to evaluate a build’s strength. Also, we can test the APIs without a user interface.
Improved Test Coverage: Most API’s have features, that allow a tester to create automated tests with high test coverage including positive and negative cases. We can rarely find test cases that can’t be automated.
Reduce Testing Cost: With API testing we can find minor bugs before the GUI testing. Usually, these minor bugs will become bigger during GUI testing. So finding those bugs while performing API testing will be cost effective.
Enables Faster Releases: The test cases that take about 8-10 hrs when executing UI regression testing take only about 1-2 hrs with API testing. This allows companies to release builds faster with API testing.
5. How to Perform API Testing?🛠
Listed below are the steps that you can follow to perform API testing:
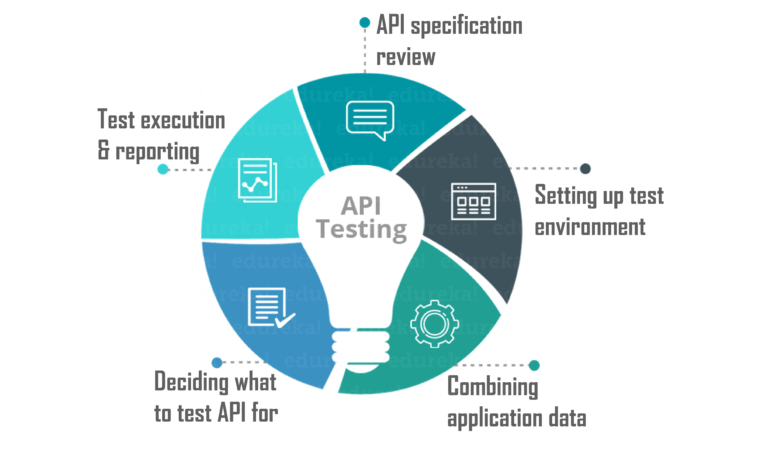
- API Specification Review
The first step is documenting the API testing requirements. What is the purpose of the API? What is the workflow of the application? Which integrations are supported by the API? What are the features of the API? Documenting all these API testing requirements is the first thing you need to do. This will help you in planning API tests throughout the testing process.
- Setting Up Test Environment
Next step is setting up a testing environment, with the required set of parameters around the API. This involves configuring the database and server for the application requirements.
- Integrating Application Data
In this step, you need to combine your application data with the API tests to ensure that the API functions as expected against all possible input configurations.
- Deciding Type of API Test
After you’ve created the testing boundaries and requirements, you need to decide what you want to test your API for. There are different types of API tests like functionality testing, validation testing, load testing, security testing, end-to-end testing, fuzz testing and many more. More about API testing types in the next session of this article.
6. Types of API Testing📊
In API testing, the following types of testing can be conducted:
- Functionality Testing – To check if the API works and does exactly what it’s supposed to do
- Reliability Testing – To check if API can be consistently connected to and lead to consistent results
- Validation Testing – Helps verify the aspects of product, behavior, and efficiency of an API
- Load Testing – Is performed to ensure the performance of API under both normal and at peak conditions
- UI Testing – It involves testing the user interface for the API and other integral parts
- Security Testing – To test that the API is secure against all possible external threats
- Penetration Testing – To detect vulnerabilities of an application from an attackers perspective
- Fuzz Testing – To test the API in terms of the limits to prepare for the “worst case scenarios”
7. API Testing Tools🔧
For successfully performing API testing, you will need a tool to structure and manage your test cases. Here are some of the top API testing tools that can be used for Rest API and Soap API:
SoapUI: It is the most widely popular open-source tool for API testing. With SopaUI you can perform functional testing, performance testing, security testing, and data-driven testing. It will provide you with the reports for testing and will allow you to export the data.
Postman: With more than 4 million users worldwide it is one of the most popular API testing tools. It runs on Mac, Windows, Linux & Chrome Apps. Allows you to set up all the headers and cookies your API expects, and then check the response.
Katalon Studio: It is a robust and comprehensive automation tool for API, Web, and mobile testing. Provides easy deployment by including all frameworks, ALM integrations, and plugins in one package. Also, supports both SOAP and REST requests,also supports various types of commands and parameterization functionalities.
Tricentis Tosca: It is a model based test API automation testing tool from Tricentis but also supports API testing. It supports a wide array of protocols including HTTP(s) JMS, SOAP, REST, IBM MQ, NET TCP, etc.
REST-assured: It is an open-source Java Domain-specific language (DSL) tool that makes testing REST service simple. Supports XML and JSON requests. This tool simplifies things by eliminating the need to use boiler-plate code to test and validate complex responses.
Apart from these popular tools, there are also tools like Apache JMeter, HttpMaster, Parasoft, HP QTP, Karate DSL, and many others. Though these tools make API testing easy, you might still come across some challenges while performing API testing.
8. What is WAF(Web Application Firewall) & Why WAF is important👨💻🔥
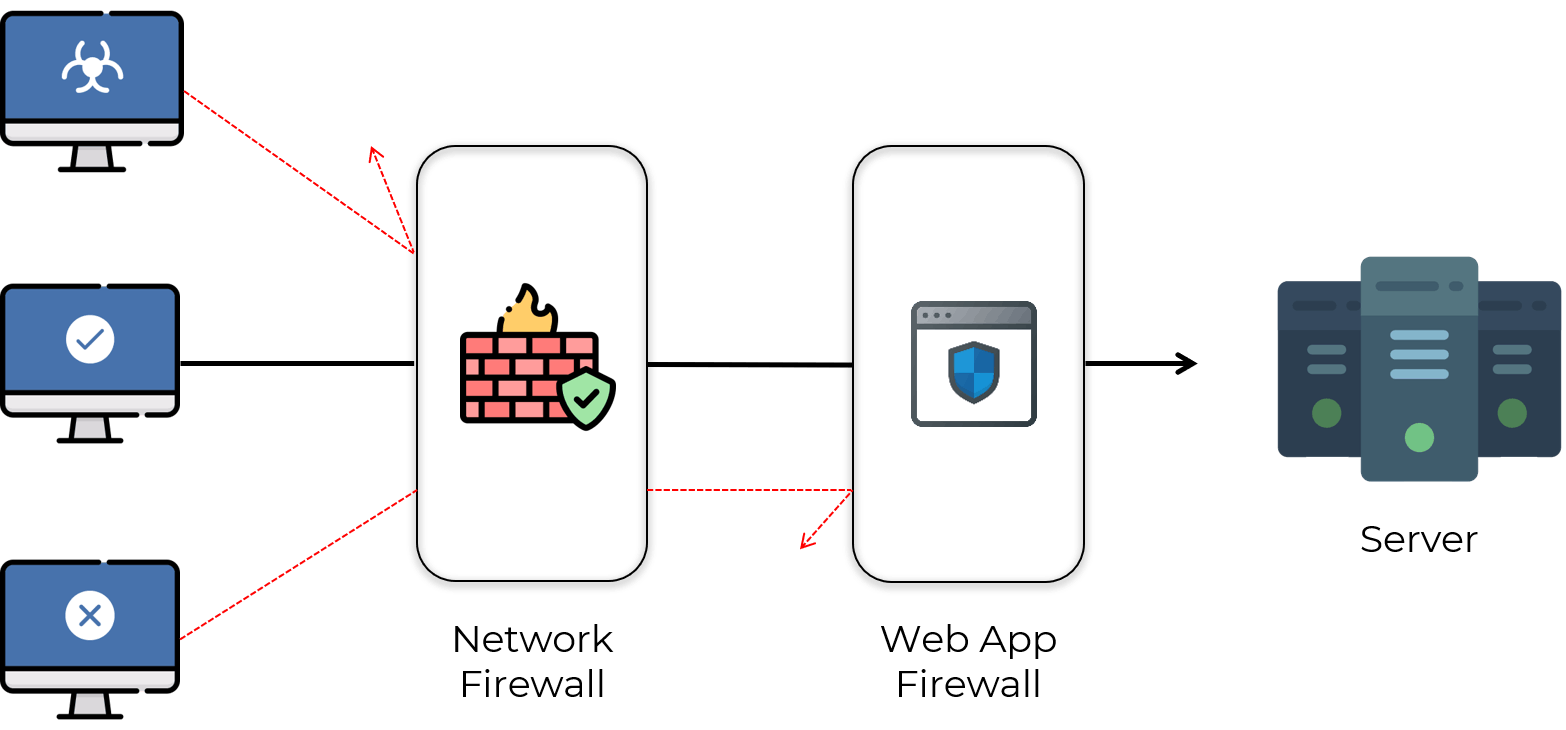
A web application firewall(WAF) is a firewall that monitors, filters and blocks data packets as they transmit to and from a website or a web application.
Web application security is important because it is the process of protecting websites and online services against different security threads that exploit vulnerabilities in an application's code.Common targets for web application attack are content management system(i.e. wordpress), database administration tools(i.e. phpmyadmin), and software as a service(Saas) application.
9. Limitation of WAF(Web Application Firewall)?🚧🔥
It is not a good strategist for protecting API using WAF(Web Application Firewall). The attacker can bypass the firewall and trigger malicious code so it not sufficient and require lot of resources.
10. What is CherryBomb ?💣

It is basically a open source tool. It is a API security system tool, it can scan an API and identify vulnerability, also it block packets where WAF(Web Application Firewall) and API security management fail to scan those packets. The BLST(Business Logic Security Testing) is the main feature that discuss below.
11. What is BLST (Business Logic Security Testing) ?👨🔬👩🔬
The BLST stands for Business Logic Security Testing identify broken business logic attack in a API. It can easily mapped the vulnerability and represent the status on dashboard. It's a fully open source tool.
12. Practical Demo👨🏫👩🏫
All the things are mention in this Github repository 💻
- Installation💽
For Linux/MacOS:
curl https://cherrybomb.blstsecurity.com/install | /bin/bash
The script requires sudo permissions to move the cherrybomb bin into /usr/local/bin/.
(If you want to view the shell script(or even help to improving it - /scripts/install.sh)
- Direct download📥
This is a binary file and you DO NOT have to install Rust. If you use this method you should run this command
mkdir ~/.cherrybomb
- Usage
To check the installation :✅
cherrybomb --version
API specification scan :
cherrybomb oas --file <PATH> --config <PATH> --verbosity <0/1/2> --format <cli/txt/json> --output <PATH>
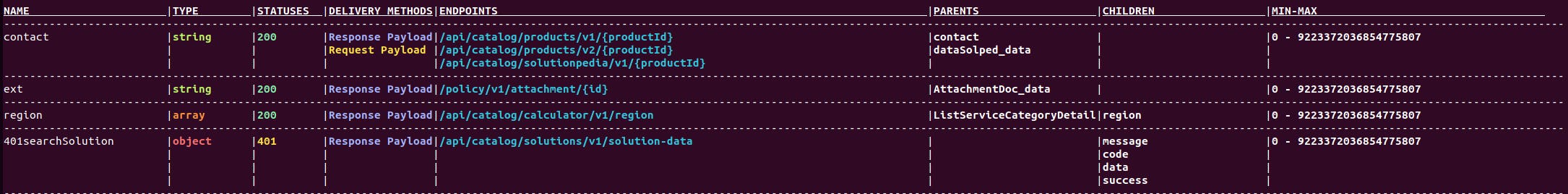
Returns Parameter Table :
cherrybomb param-table --file <PATH> --name <SINGLE PARAM NAME(OPTIONAL)>
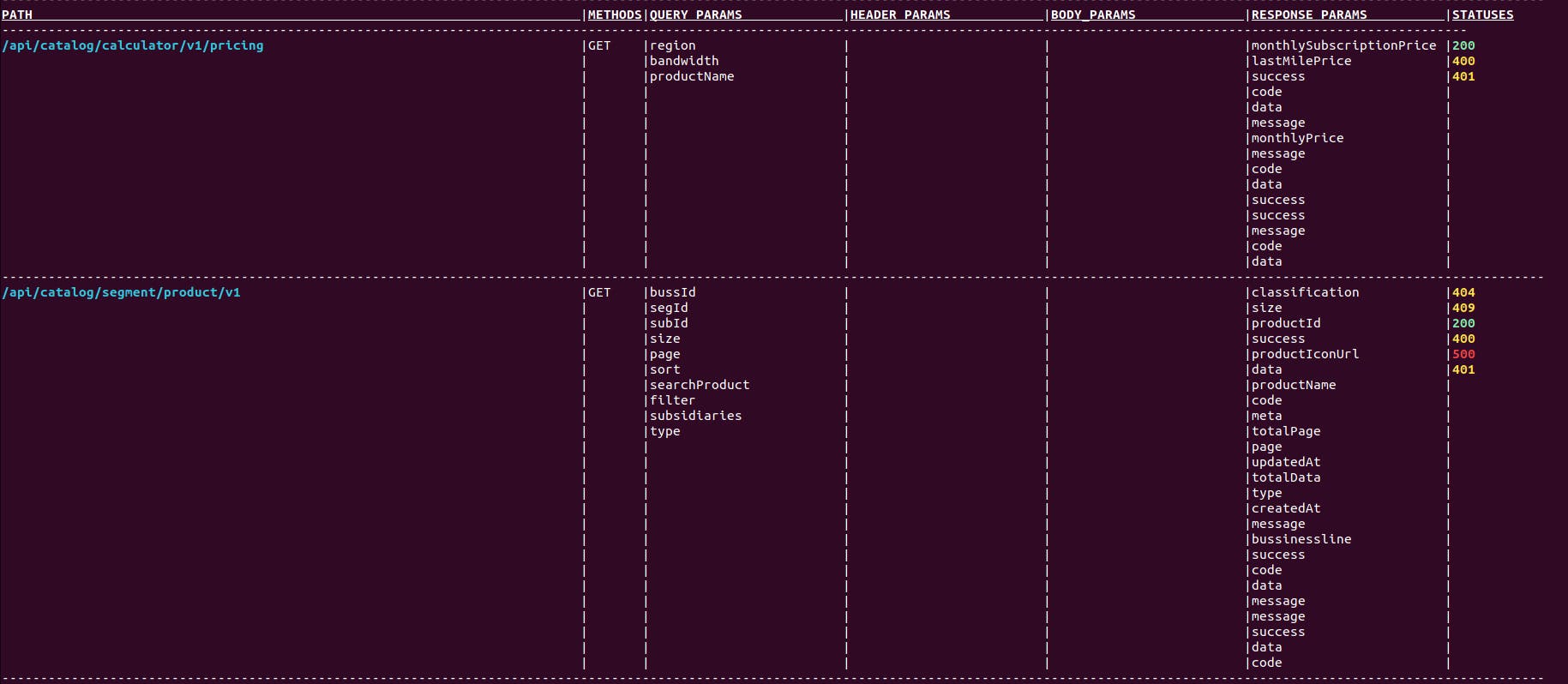
Returns Endpoint Table :
cherrybomb ep-table --file <PATH> --name <SINGLE PARAM NAME(OPTIONAL)>
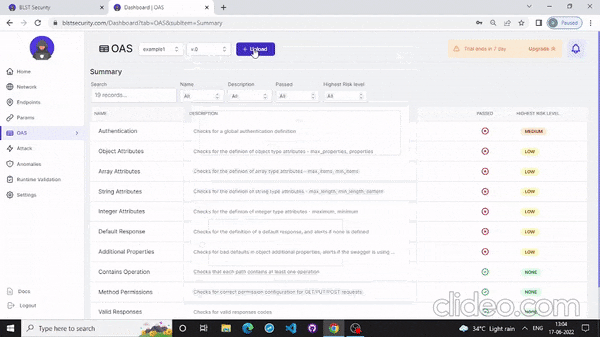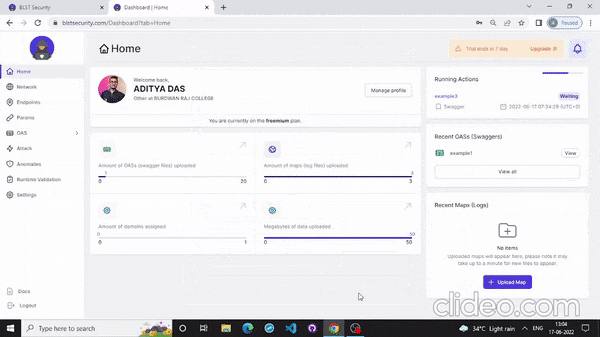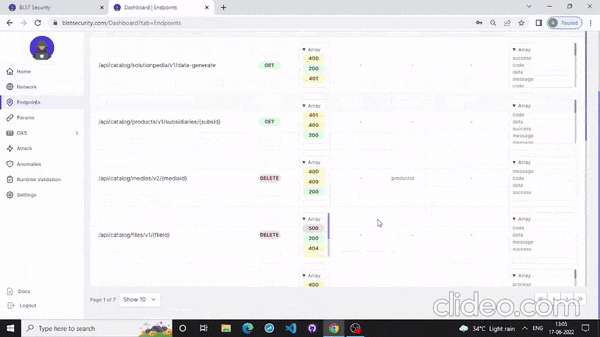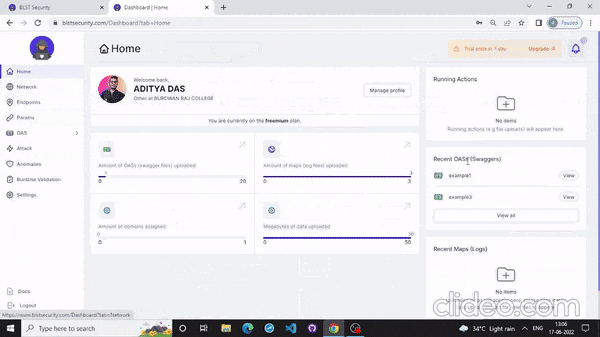
- Also you can scan your API from the website that mention below:
- Conclusion & references🚩
Some next level 🎸resources are mention below, check it out 👇👇
🔗 blstsecurity.com/?promo=cy_6188f93119418000..
🔗 github.com/blst-security/cherrybomb
To add additional resources feel free to reach out to me 👀 📡📺🛰
Twitter 🖱
Linkedin 🖱
GitHub 🖱
